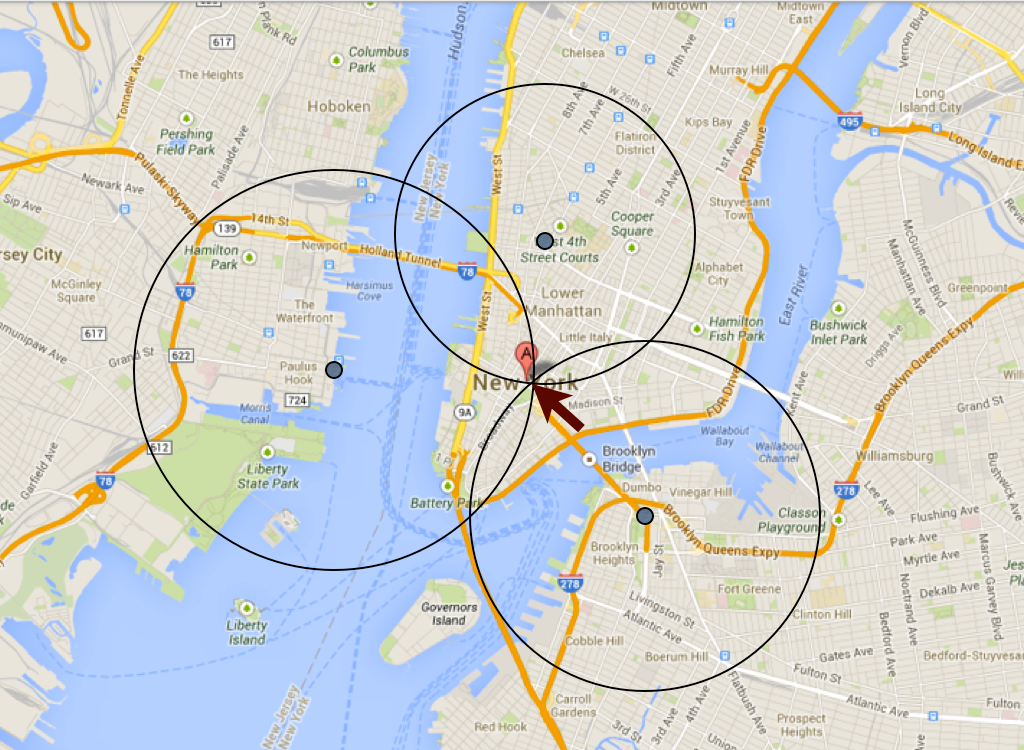
Users of the dating app Tinder were able to pinpoint each others’ locations until the end of last year, according to Internet security researchers, a flaw that highlights the vulnerabilities of mobile apps that use location-based technology.
For months until the end of 2013, Tinder users who knew how to do so were able to see how close they were to each other in increments of 100 feet. By using rudimentary programming skills, users could mine Tinder data to find out where any other user was. To do this, someone would need to use three different accounts as a way to triangulate a target’s location, according to research by Internet security consultant Include Security. Tinder is a popular dating app that allows users to see pictures of nearby users and look for matches.
“The vulnerability allowed one Tinder user to triangulate the location of another Tinder user within 100 feet,” said Erik Cabetas, the managing partner of Include Security. “You don’t need any special privilege or anything like that. All the information is gathered from the server with any Tinder user account.”
(MAGAZINE: The New Dating Game)
It’s unclear if any users actually exploited the security flaw. Tinder did not immediately comment on Wednesday.
Include Security is an independent consultant that probes networks for large tech clients but flexes its hacking muscles in between major assignments. That’s how it says it first exposed the Tinder flaw last October. After notifying the dating application’s CEO, Sean Rad, Include Security received an acknowledgement and a thank-you from the company. But Cabetas said Include Security saw no change to Tinder’s security until Jan. 1, even after repeatedly checking to see whether triangulating users’ location was still possible.
Tinder will now only show users’ locations in increments of a mile, Cabetas said, making triangulation much less precise.
“Without the high precision we can’t do the triangulation,” Cabetas said. Though users can no longer exploit the flaw, other companies may face similar location issues, Cabetas added: “This vulnerability will become more common as applications add location-aware features.”
More Must-Reads from TIME
- Why Trump’s Message Worked on Latino Men
- What Trump’s Win Could Mean for Housing
- The 100 Must-Read Books of 2024
- Sleep Doctors Share the 1 Tip That’s Changed Their Lives
- Column: Let’s Bring Back Romance
- What It’s Like to Have Long COVID As a Kid
- FX’s Say Nothing Is the Must-Watch Political Thriller of 2024
- Merle Bombardieri Is Helping People Make the Baby Decision
Contact us at letters@time.com