Cell phones — particularly smartphones — are inherently bad for privacy. You’ve basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, the handset’s data connection ensures that tracking cookies, advertising IDs, and usage stats follow you around the internet.
So no, there’s no such thing as a perfectly secure and truly private smartphone, let’s get that out of the way now. But in the information age, you practically need a smartphone just to get by in society, so the question then becomes: Which phone manages to be the lesser of all the evils?
With critical vulnerabilities such as the Dirty COW exploit on Android and the Pegasus NSO hack on iOS, not to mention the FBI attempting to find a backdoor into practically every phone, that’s a hard question to answer. So to find the most security-hardened devices, we tested the top smartphones on the market, looking for key factors like encryption strength, biometrics, VPN availability, and security patch time frames. Our research narrowed the list down to four great phones, so let’s discuss how well each of these devices protects your privacy.
Key Comparison Points
When it came to comparing our four finalist phones, these were the key differentiating factors for privacy and security:
Read more: How Thieves Unlock Passcodes on Stolen iPhones (And How to Protect Yourself Against It)
How We Chose These Phones
Our first requirement in choosing these phones was that they all had to be available for sale in the United States. Secondly, for a phone to make this list, it had to be encrypted by default to ensure that your data is protected against external access.
Another requirement was that the phones all offered granular permission management, which allows you to revoke an app’s permission to access certain features like your camera and microphone. Then, to ensure that your data remains safe even when your phone is lost or stolen, we only selected phones with remote lock and wipe capabilities.
From there, finalists were chosen based on how well the devices scored in the key comparison points above, and with that, the following phones rose to the top.
1. Blackphone 2

Startup manufacturer Silent Circle is a company that focuses on privacy and security in all of its products and services. Their second smartphone, the Blackphone 2, is powered by a security-focused fork of Android called Silent OS, which features privacy enhancements such as a security center that allows you to control what data apps can access (more on this later).
Silent Circle apparently subscribes to the school of thought that says biometrics are bad for security, as they’ve chosen not to include a fingerprint scanner on their Blackphone 2. This means that you won’t be able to log into your LastPass account with your fingerprint, though, as an Android device, the Blackphone has the ability to auto-populate LastPass passwords into text fields and apps, so it’s still a fairly easy process.
The Blackphone 2 uses 128-bit AES encryption, though it’s of the full disk variety, meaning once the decryption key (your PIN or password) has been entered, the entire data partition is decrypted. This is still a very secure implementation, but encryption is handled entirely by software, so it can have an impact on device performance when compared to a handset like the iPhone, which uses a hardware encryption engine.
As an Android device, the Blackphone 2 has the ability to maintain separate user spaces. But to make things even better, Silent Circle has added a few additional undisclosed security measures to ensure that the data from each user account is completely inaccessible while logged into a different account. This feature would be particularly handy if you want to maintain a secondary, more secure user account that isn’t logged into Google Services.
Speaking of Google Services, the Blackphone 2 will not let you limit the ability of apps to see and use Google’s ad tracking identifier for your device, so you might want to periodically reset the ad tracking data in Settings -> Google. However, the Blackphone 2 gives you the option of installing an encrypted VPN app and using it on both Wi-Fi and cellular data, so the rest of your internet traffic can be completely anonymous. Additionally, you can use the same VPN feature to selectively block all internet access to individual apps.
Another major bonus when it comes to anonymity is the fact that each Blackphone 2 comes with a full year of Silent Circle’s encrypted phone call and messaging service for free, so even your carrier won’t be able to intercept your communications. On top of that, the Blackphone 2 has another awesome feature called CIDS (Cellular Intrusion Detection System), which notifies you when the device connects to a suspicious cell tower, in an attempt to protect your calls and text messages against StingRay surveillance devices used by government agencies.
The Blackphone 2 will automatically trigger a full data wipe after 10 failed login attempts, so you can rest assured that a brute-force password hack won’t allow anyone to log into your phone. Then, to make things even more secure, Silent Circle has included a Security Center app that resides right on the home screen dock. The device automatically prevents apps from accessing sensitive information like your location or camera, and the Security Center app serves as the only way to reenable these permissions.
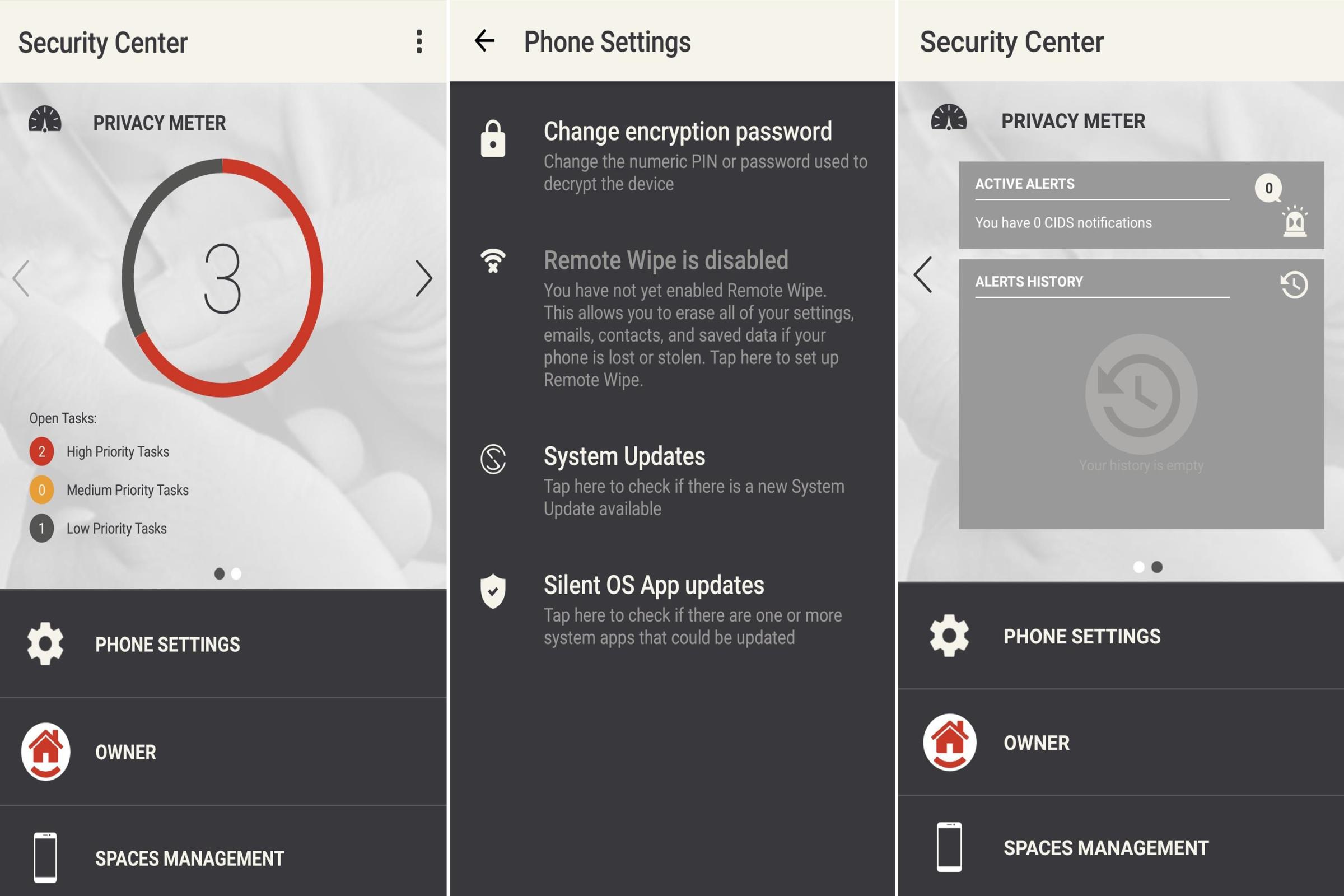
Silent Circle has their own bug bounty for the Blackphone that rewards up to $1,024 for any bugs found, and the program is open to the public. And as a sort of cherry on top, the Blackphone 2’s single, most important security feature may very well be the fact that Silent Circle has promised to issue security updates within 72 hours of a critical bug being discovered, which tops all devices in this list by a considerable margin.
Buy it here
Read more: 7 Ways to Bypass Android’s Secured Lock Screen
2. BlackBerry PRIV

Even though the PRIV is over a year old, it’s still BlackBerry’s newest flagship device. The PRIV was BlackBerry’s first Android phone, but they’ve since gone all-in on the Android ecosystem with two additional midrange phones in the DTEK50 and DTEK60. That hasn’t changed BlackBerry’s legendary security-first approach, as the PRIV has several privacy enhancements layered on top of its core Android code base — and another signature BlackBerry feature made the cut in the form of the PRIV’s slide-out mechanical keyboard.
Like the Blackphone 2, the PRIV does not have a fingerprint scanner, which can be a positive or a negative depending on how you want to look at it. However, this does mean that you won’t be able to log into LastPass with your fingerprint, but you the app can still auto-populate passwords for you.
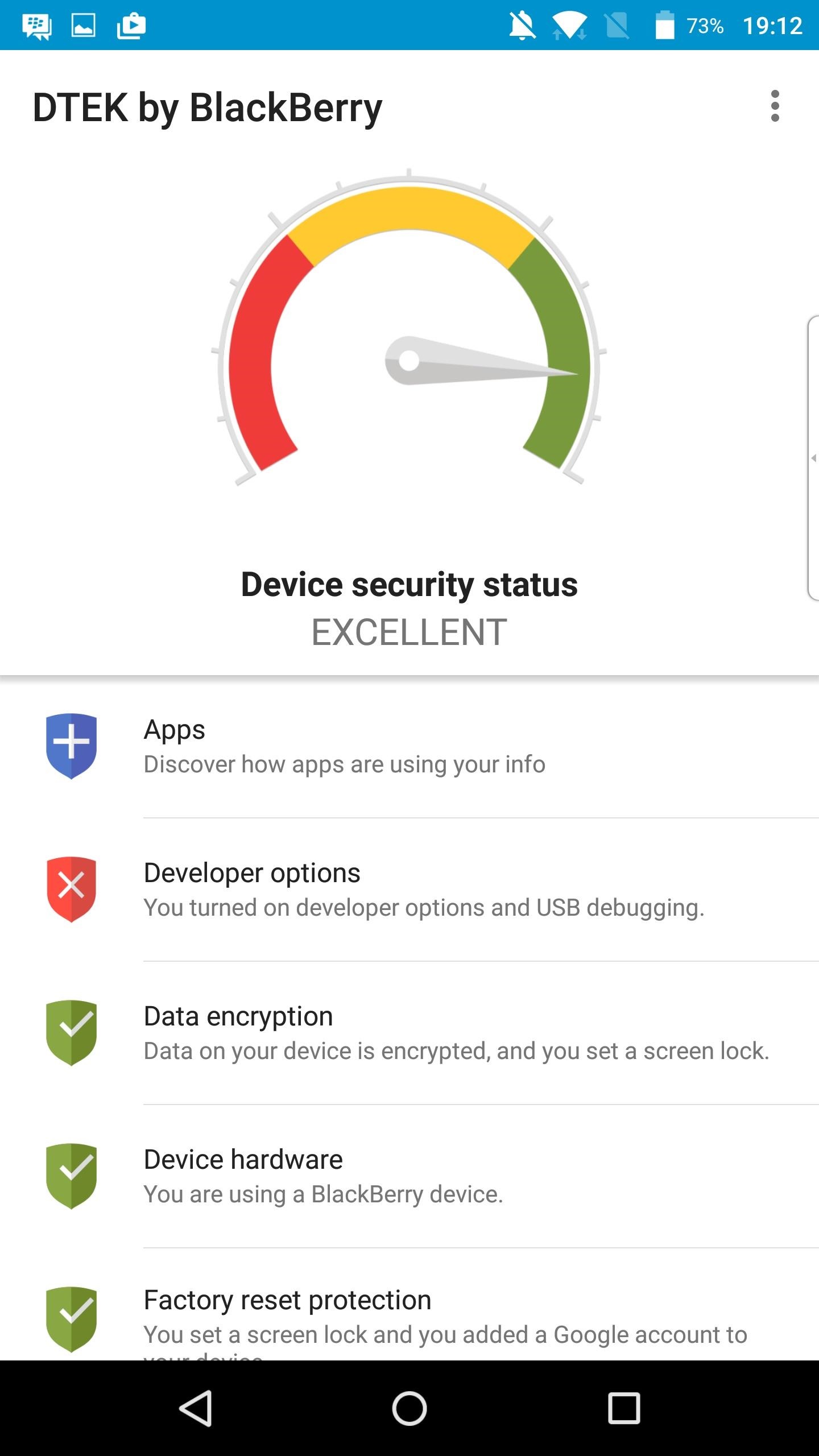
The PRIV uses full disk encryption powered by a software-based encryption engine, which are two minor downsides relative to some other phones in this list, but still very strong security measures when compared to the rest of the smartphone market. To make the encryption even stronger, it’s using 256-bit AES keys, which means there’s 2 to the power of 256 possible combinations — a number so big that we don’t even have a word for it.
With the help of its Android-powered operating system, the PRIV will let you create sandboxed user profiles that don’t share any data between them, which is perfect for keeping your work and personal life separate. On top of that, Android allows the PRIV to use always-on VPN services to encrypt internet traffic on Wi-Fi and mobile data, as well as block internet access to individual apps. However, one downside to Android and its bundled Google Services is the fact that you cannot truly limit ad tracking like you can on the iPhone.
The PRIV will automatically wipe all user data when someone enters the wrong password or PIN ten times, which is a security measure BlackBerry has added on top of stock Android. And much like Silent Circle’s approach with the Blackphone 2, BlackBerry has included a security center app called DTEK that will help you keep track of app permissions and inform you when there’s a security issue that needs to be addressed.
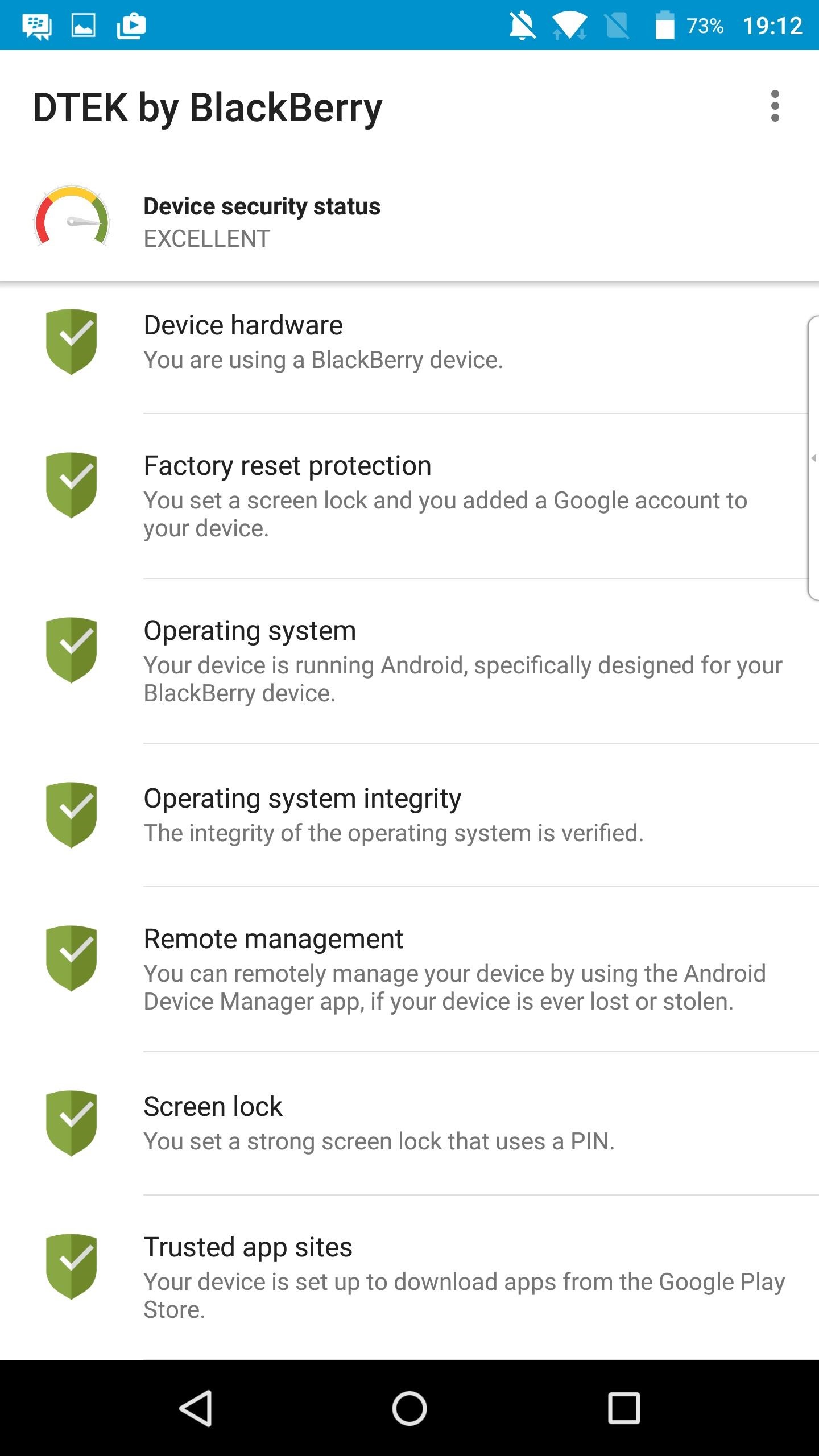
BlackBerry is committed to Android’s monthly security patch program, and they’ve stated that they will go a step further and issue faster updates if a critical security bug is ever found. The company also has a bug bounty program for its devices, but they don’t disclose how much they’re willing to pay when a programmer finds a security flaw in their software.
Buy it here
Read more: See Passwords for Wi-Fi Networks You’ve Connected Your Android Device To
3. iPhone 7

The iPhone 7, together with the iPhone 7 Plus, has helped Apple to reclaim the title of top smartphone maker in the world, as of Q4 2016. Top to bottom, it’s an expertly crafted smartphone with benchmark scores that top the market (thanks to an insane spec sheet). However, it’s the iPhone’s security features that plant it firmly in this particular list.
The iPhone’s Touch ID fingerprint scanner allows you to log into your phone in one tap, and the same feature works with numerous banking apps and similar services, such as LastPass. Depending on your line of thinking, you may view biometrics as a security risk, but you have to admit that Touch ID makes folks more likely to use longer, more secure passwords with their online services, since they can log into their accounts by touching a button instead typing out a complicated password.
The iPhone 7 uses AES 256-bit file-based encryption, which is as good as it gets with smartphones. This is powered by a dedicated hardware encryption engine, which contributes greatly to the device’s top-notch read and write speeds.
Though the iPhone 7 does not offer a security center app, it does have a robust Privacy menu that allows you to restrict usage of the device’s unique ad-tracking identifier. Enabling the “Limit Ad Tracking” option here will ensure that apps do not use your device’s unique identifier in any way other than for “limited advertising purposes.” This is different than the Android devices in this list, which will let you reset your ad-tracking ID and even opt out of being served targeted ads, but will not allow you to limit apps’ abilities to view and use your unique ID.
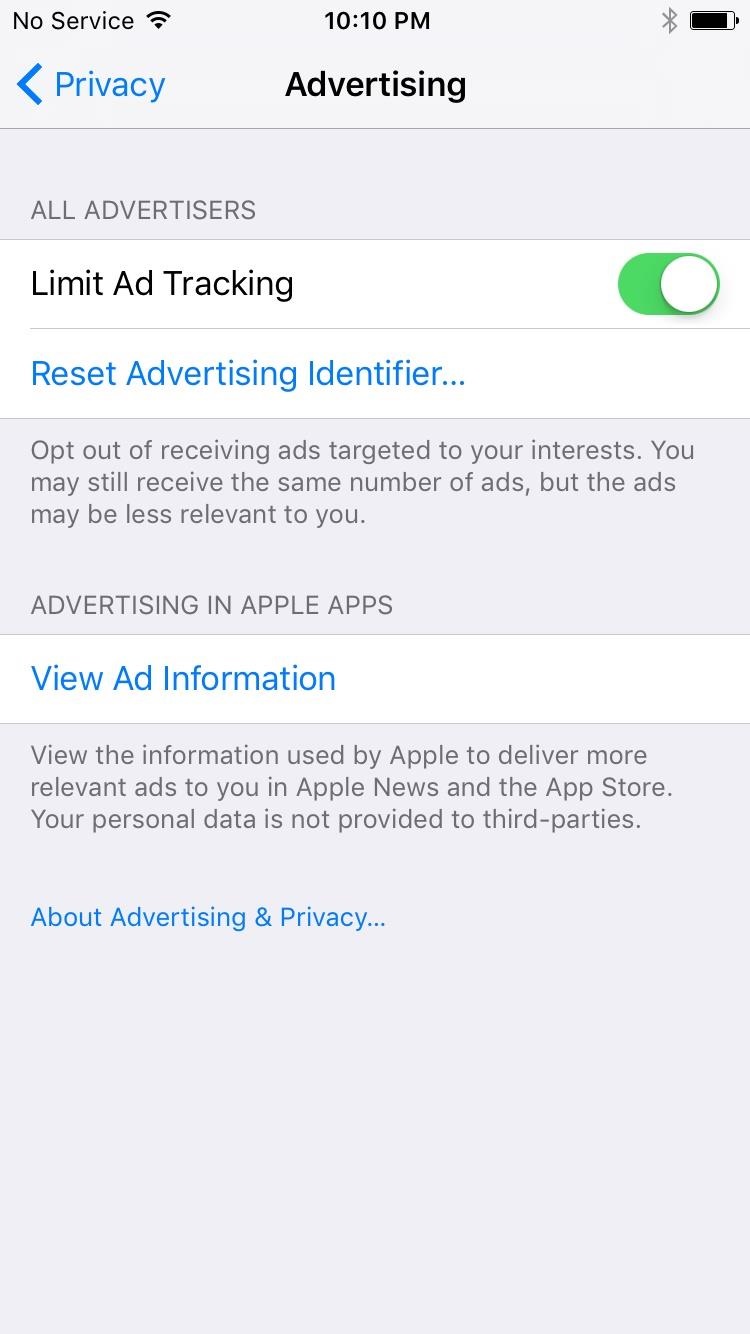
Judging by public perception after the San Bernardino shooting investigation where Apple refused to create a backdoor for the FBI, as well as all of the above positives, you’d think the iPhone clearly outranks all Android devices in terms of security. But with feature phones like the PRIV and Blackphone that were purpose-built to appeal to privacy-minded users and the enterprise sector, there are a few key areas where Apple lags behind.
Apple has a bug bounty program for its iOS devices, as well as its iCloud service, and they offer more than any other manufacturer here for finding a critical issue (up to $200,000). But the program is not open to the public, so the pool of programmers working to find bugs is severely limited (just “a few dozen” invited researchers, according to Apple). It’s worth noting, though, that other companies offer bug bounty programs for Apple devices, so that may help to offset this problem.
Other downsides are the lack of sandboxed user spaces, as well as the fact that you have to reset the device and enable “Supervised Mode” if you want to use an encrypted VPN service with your mobile data connection instead of just Wi-Fi.
Back on the positive side, you should know that Apple has an excellent track record when it comes to patching critical vulnerabilities found in iOS. It only took them two weeks to issue a fix for the Pegasus NSO hack, and just over a month to plug up the 911 bug in iOS 10, so backdoors are closed almost as quickly as they’re found.
On a final note, these same privacy features apply to all of Apple’s current-generation smartphones. We’re recommending the iPhone 7 here as it offers the best balance of specs and pricing, but you can go with an iPhone 7 Plus if you like a bigger phone, or an iPhone SE if you want to save some extra money while sacrificing a few bonus specs like screen size.
Buy it here
4. Google Pixel
The Pixel and its bigger brother, the Pixel XL, are the first phones made by Google, yet they’ve already been an all-around success in terms of sales and general reception. As the only Android device in this list that wasn’t a purpose-built security “feature phone,” the Pixel still garners consideration in large part due to two factors that differentiate it from the rest of the Android pack: timely updates directly from Google, and file-based encryption. Couple that with the phone’s top-notch specs, and it’s worth a consideration on multiple levels.
The Pixel’s fingerprint scanner, dubbed Pixel Imprint, works much the same as Apple’s Touch ID in that it allows you to unlock your phone easily and even log into apps and services. Combined with Android’s ability to let the LastPass app auto-populate your complicated passwords, this means that the Pixel is the only phone in this list that will let you use LastPass to log into apps and websites by simply touching the fingerprint scanner.
The Pixel uses a software-based encryption engine, which has been known to slow down read and write speeds on some devices. However, it’s one of the only Android phones to date that uses file-based encryption, which gives the device an extra layer of security to go along with its 256-bit AES decryption key.
The Pixel will let you create sandboxed user spaces that do not share any personal data, so you can keep your work and personal life separate. In addition to that, you can set up a system-wide VPN to encrypt traffic on Wi-Fi and mobile data connections alike, and this same feature can be used to block apps from accessing the internet altogether.
As for downsides, the Pixel does not allow you to restrict apps’ access to your device’s unique advertising identifier, so you’d be well served to periodically reset this ID number. There’s also no security center app, so you’ll have to dig around in Settings to manage app permissions and other privacy options. Finally, the Pixel does not automatically wipe data after too many failed logins, which leaves the device susceptible to a brute-force password or PIN attack.
But on the bright side, Google has perhaps the best bug bounty program of all the manufacturers in this list. They’ll offer up to $50,000 for critical bugs found, and the program is open to the public, so there should always be plenty of folks scouring the Pixel’s code base for security loopholes. And as Google is the primary maintainer of the entire Android operating system, the Pixel has strong software support, as it gets security updates on a monthly basis.
Buy it here
Conclusion
The Blackphone 2 is genuinely a cut above the rest when it comes to privacy and security. With standout features such as its StingRay detection, as well as the free year of encrypted calls and messages, you can just tell that this device was built from the ground up with one thing in mind — privacy.
Having said that, you may not need (or even want) these over-the-top privacy features, and perhaps a solidly-secure phone with top-notch specs is more up your alley. If that’s the case, the BlackBerry PRIV ticks a lot of boxes in terms of both hardware and security, while the iPhone and Pixel both knock it out of the park when it comes to specs, and simultaneously offer solid security options.
This article originally appeared on GadgetHacks.com
More Must-Reads from TIME
- Cybersecurity Experts Are Sounding the Alarm on DOGE
- Meet the 2025 Women of the Year
- The Harsh Truth About Disability Inclusion
- Why Do More Young Adults Have Cancer?
- Colman Domingo Leads With Radical Love
- How to Get Better at Doing Things Alone
- Michelle Zauner Stares Down the Darkness
Contact us at letters@time.com