
We’re living in the age of the data breach. From Target to Home Depot, a growing number of companies have been targeted by hackers hoping to score customers’ personal data and credit card numbers.
Unfortunately for consumers, there’s little we can do to be sure the companies we’re shopping at are doing enough to prevent these kinds of incidents. However, we can take precautions to secure ourselves in case our personal information is ever stolen.
What should we do to stay safe from identity theft and fraud? Mark Risher, Google’s spam and abuse chief, offers these tips:
Keep your software updated
Updating software, whether it be on your phone, laptop, or television, is extremely important. When hackers discover new ways to steal your data, gadget and software companies usually work quickly to release fixes for those vulnerabilities. But it’s up to us to actually install those updates — or set it so that updates occur automatically.
“We’ve done some research and it’s something security experts themselves are very good at, but the general public is not,” says Risher.
Don’t fall for “phishing” scams
Phishing is an age-old technique in which users are tricked into submitting their login credentials on a fake website, only to have that information sent to hackers instead. Risher says these cons are becoming more difficult to spot.
“In the past, these phishing sites were greedy and clumsy,” he says. Older scams might have redirected users to a website that looked sketchy, asking for multiple account passwords without imitating the style or look of any particular company’s website. Today, the scams are “more simple,” Risher says. “They just copy the exact page you’re used to seeing and put it in a social context that’s misleading.”
The best ways to avoid phishing scams is by closely examining a website before you enter any login data. Pay close attention to the URL, which will often display a Web address that’s slightly different than the website it’s imitating. The same is true of email phishing scams; tricksters will often use an email address that looks legitimate but may be a character off from a company’s actual email address.
Add recovery contact info to your accounts
If your account is compromised, companies will probably try to let you know. But that’s only possible if they have some means of getting in touch with you on file.
“Add a phone number [or] an alternate email address, so that in the event you can’t log in, we have other channels where you can verify that the account is yours,” Risher says.
Don’t use the same password for multiple sites
If there’s one cardinal sin when it comes to online security, it’s using the same password over and over again across different services. This, says Risher, can be worse than never changing an old password.
“It’s much more important that you have unique passwords across all of the different sites that matter,” he says. There’s a reason many people are guilty of this: Passwords are difficult to remember. Using a password manager like LastPass or 1Password, which generate new unique passwords on your behalf each time you log in to a website, could fix this problem.
Enable two-factor authentication
Two-factor authentication adds an extra layer of security to your accounts by requiring another code in addition to your memorized password. That code can be sent to your smartphone via a text or generated by an app.
With two-factor authentication, even if a hacker has your username and password, he or she won’t be able to access your account unless they also have your smartphone — not a likely scenario.
“If you’re trying to defend yourself against getting hacked, you have to make sure everything is sealed off,” says Risher. “In your house, you would make sure that your doors are locked, that your windows are closed, that your shades are down, that you don’t have any places that people can climb through. And the bad guys just have to find one of them.”
The 10 Most Ambitious Google Projects


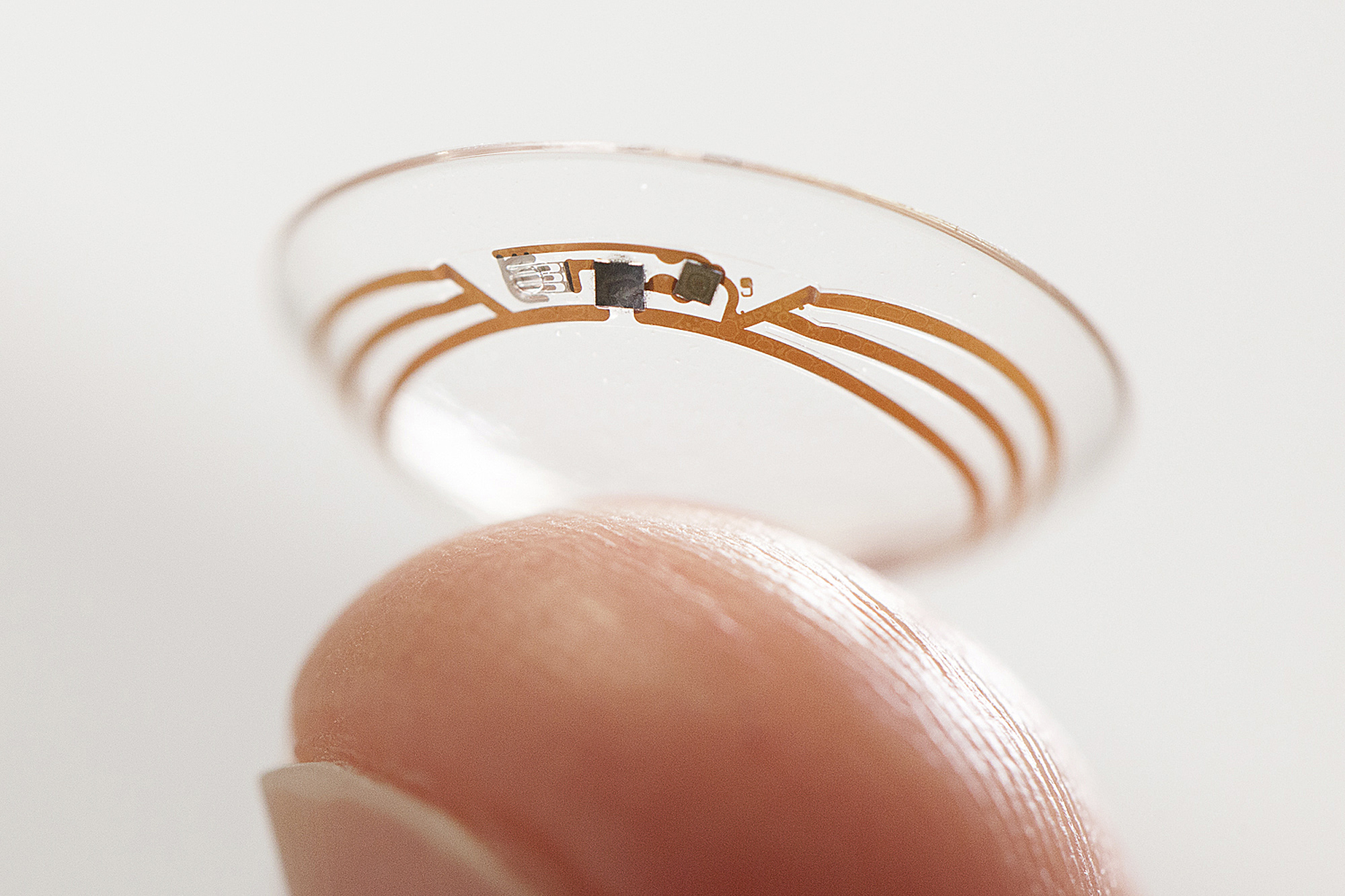






Google is one of many companies researching ways to replace or enhance the traditional password. In 2013, for example, the company said that it was looking into login methods that involve plugging in a USB dongle rather than typing in credentials.
“As people are using mobile devices, this presents whole new ways that we have to look at the problem,” says Risher. “It’s definitely an active area that we’re investing in; we’ve got some exciting stuff coming.”
More Must-Reads from TIME
- How Donald Trump Won
- The Best Inventions of 2024
- Why Sleep Is the Key to Living Longer
- Robert Zemeckis Just Wants to Move You
- How to Break 8 Toxic Communication Habits
- Nicola Coughlan Bet on Herself—And Won
- Why Vinegar Is So Good for You
- Meet TIME's Newest Class of Next Generation Leaders
Contact us at letters@time.com